whataproof
Whataproof is a decentralized anonymous content distribution platform with copyright protection. The app is perfect for selling financial research from research firms or confidential information from commercial organizations. Our solution can protect government files..
Project Description
whataproof is a decentralized anonymous content distribution platform with copyright protection. Our project is perfect for selling financial research from research firms or sharing confidential information from commercial organizations. Our solution can also protect government information.
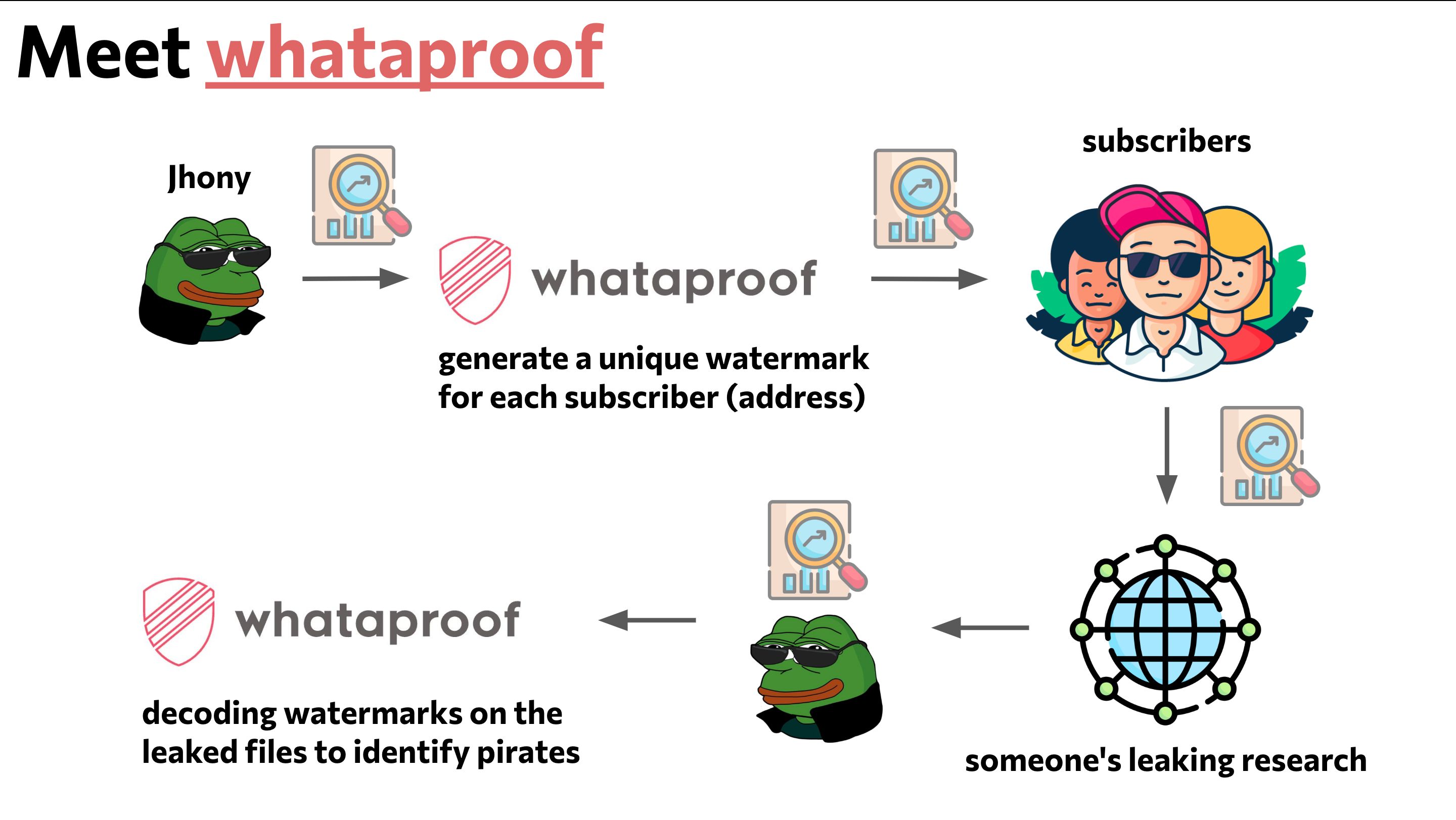
The platform comes with built-in anti-piracy mechanisms. We create a unique watermark for each user, which we embed into the content using LSB steganography technology. Thus, if someone compromises the content and publishes it openly, the author can decode the recipient and remove them from the content consumer list for copyright infringement.
Motivation
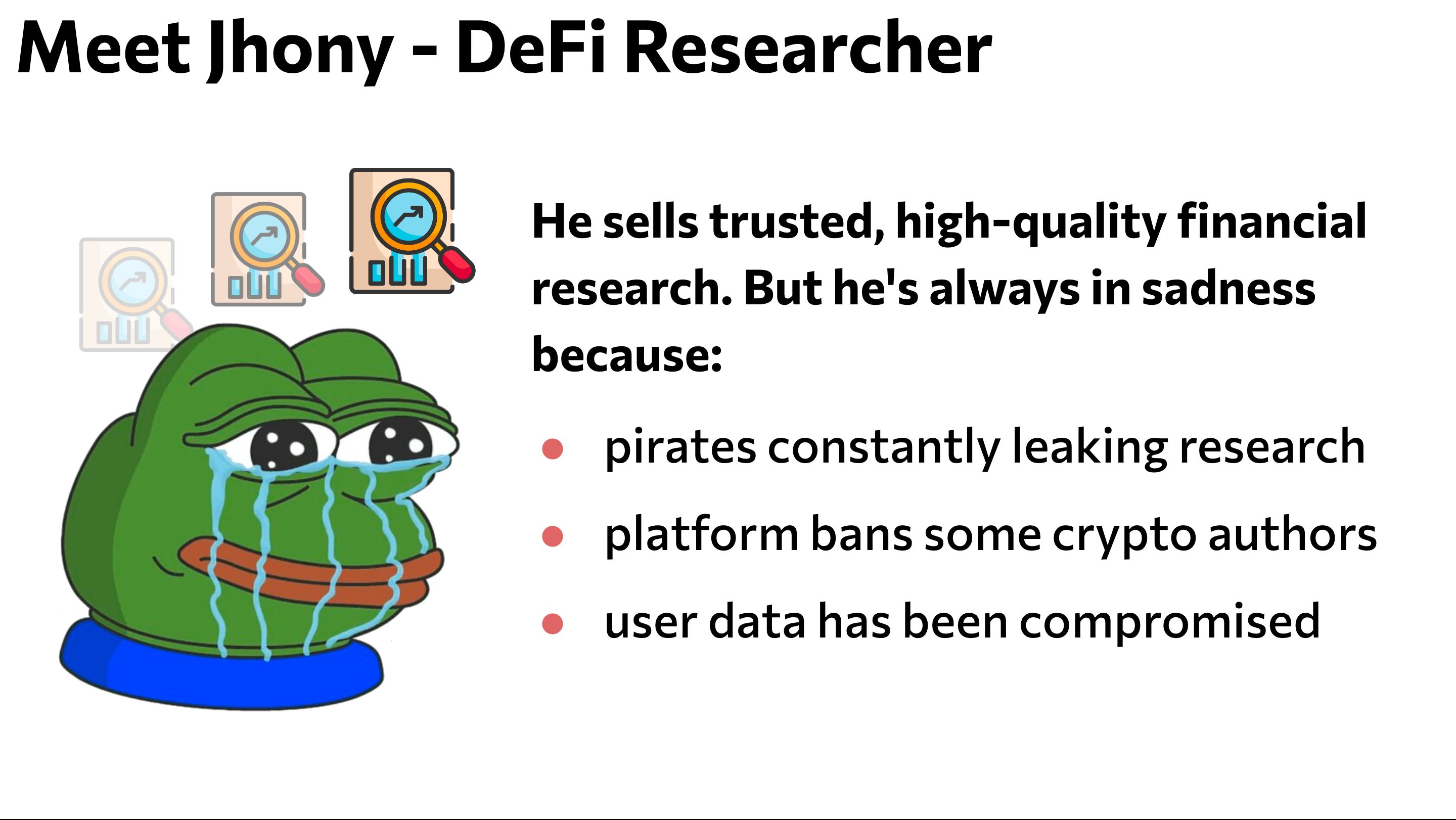
The experience of one of our team members, who created and sold DeFi Yield Farming research in a private community, inspired our idea. We want to use a decentralized solution for selling such research, which could also counteract the free distribution of these DeFi Yield Analyses in other chats. After conducting market research, we didn't find similar solutions, especially among web3 projects.
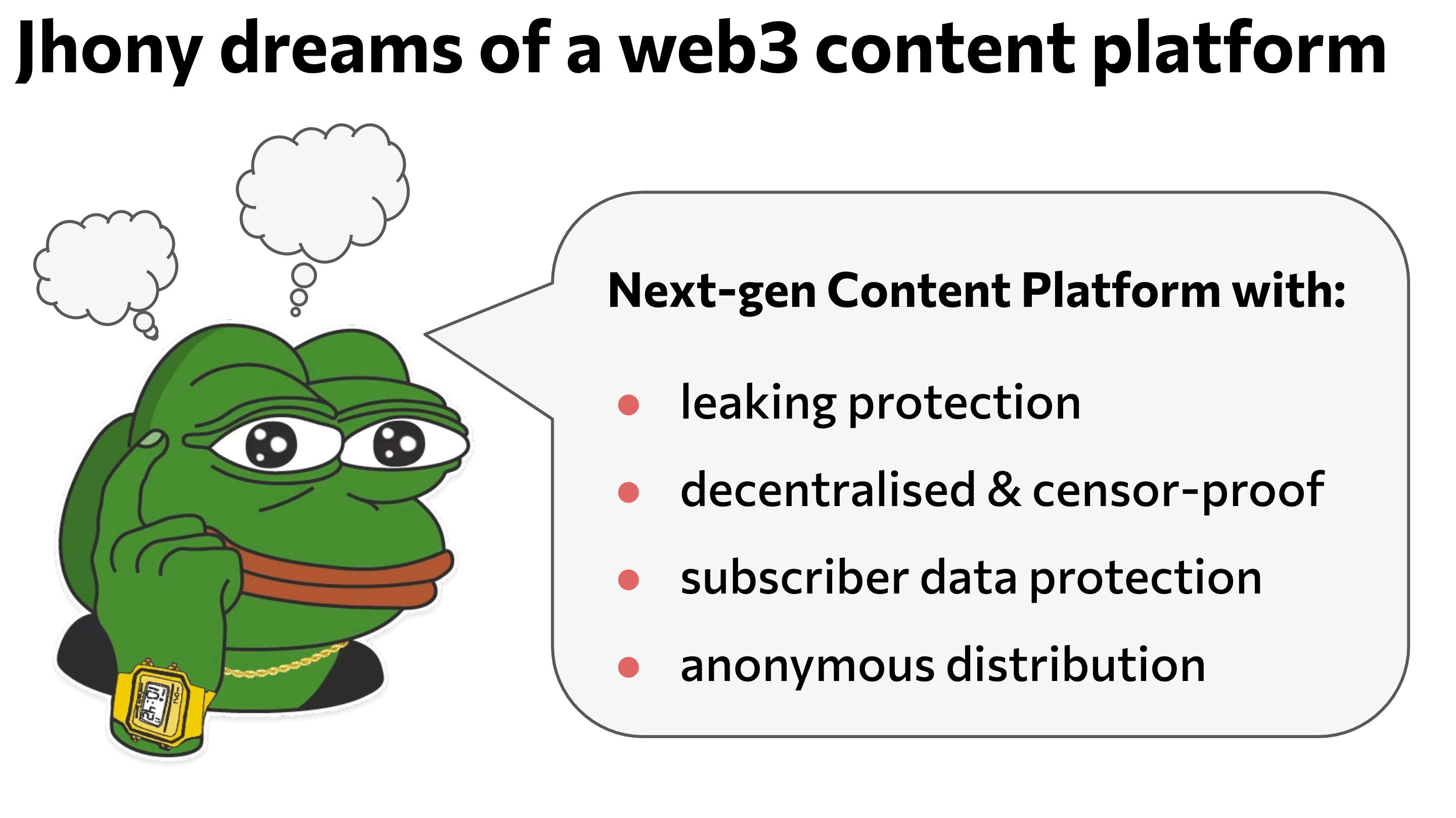
The main features of whataproof:
- Leakage protection
- Decentralization and censorship resistance
- Subscriber data protection
- Anonymous content distribution and viewing
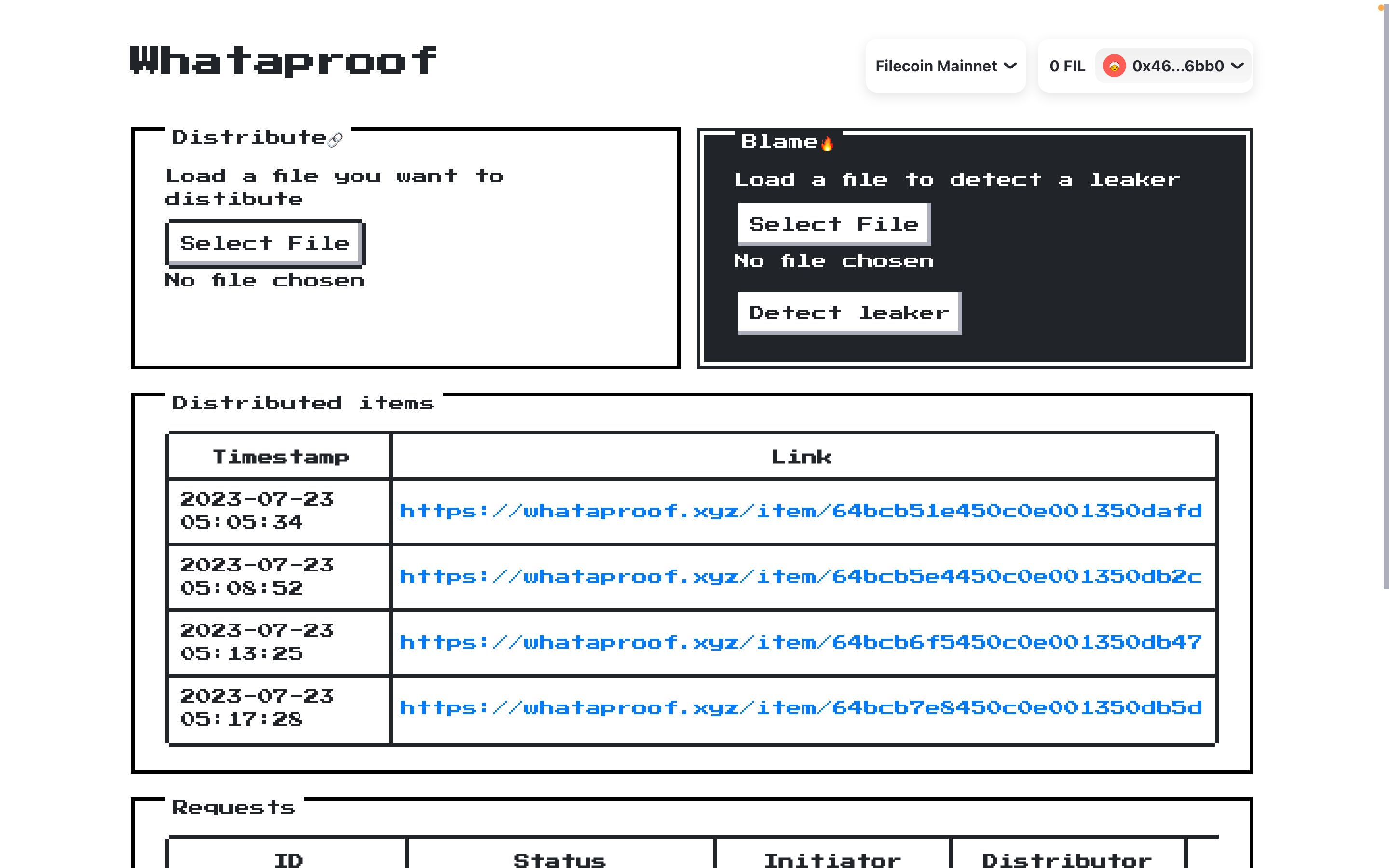
Here is the link to the demo → https://whataproof.xyz/
Here's how subscribers gain access to the creator's content:
- The content creator uploads their material to the platform.
- The platform embeds an invisible watermark into the content.
- The platform provides a link for content distribution.
- The content creator shares this content with subscribers.
- Subscribers send a request for access to the content.
- The content creator confirms or denies the request.
- Subscribers gain access and can view the content.
Here's how the process of finding and blocking pirates works:
- The content creator finds their content openly available.
- The creator uploads compromised content to the platform.
- The platform decodes the original recipient's address from the content.
- The content creator removes the pirate from the subscriber list.
Monetization and Growth
If we win the ETH Global Paris hackathon with this idea, we will continue to validate it and look for a product-market fit for Whataproof. Regarding functionality, we plan to integrate invisible watermarks into text, audio, and video files. We will implement decentralized payment systems, such as Curra.io.
In the full version of our product, we plan to incentivize users further to protect content from piracy. Subscribers will make an anti-piracy deposit to gain access to the content. Anyone can check the compromised file and receive a reward for detecting pirates.
From the moment of launch and integration of payment systems, our platform will be able to charge 1% of the volume of content sales by creators as a fee for using our platform.
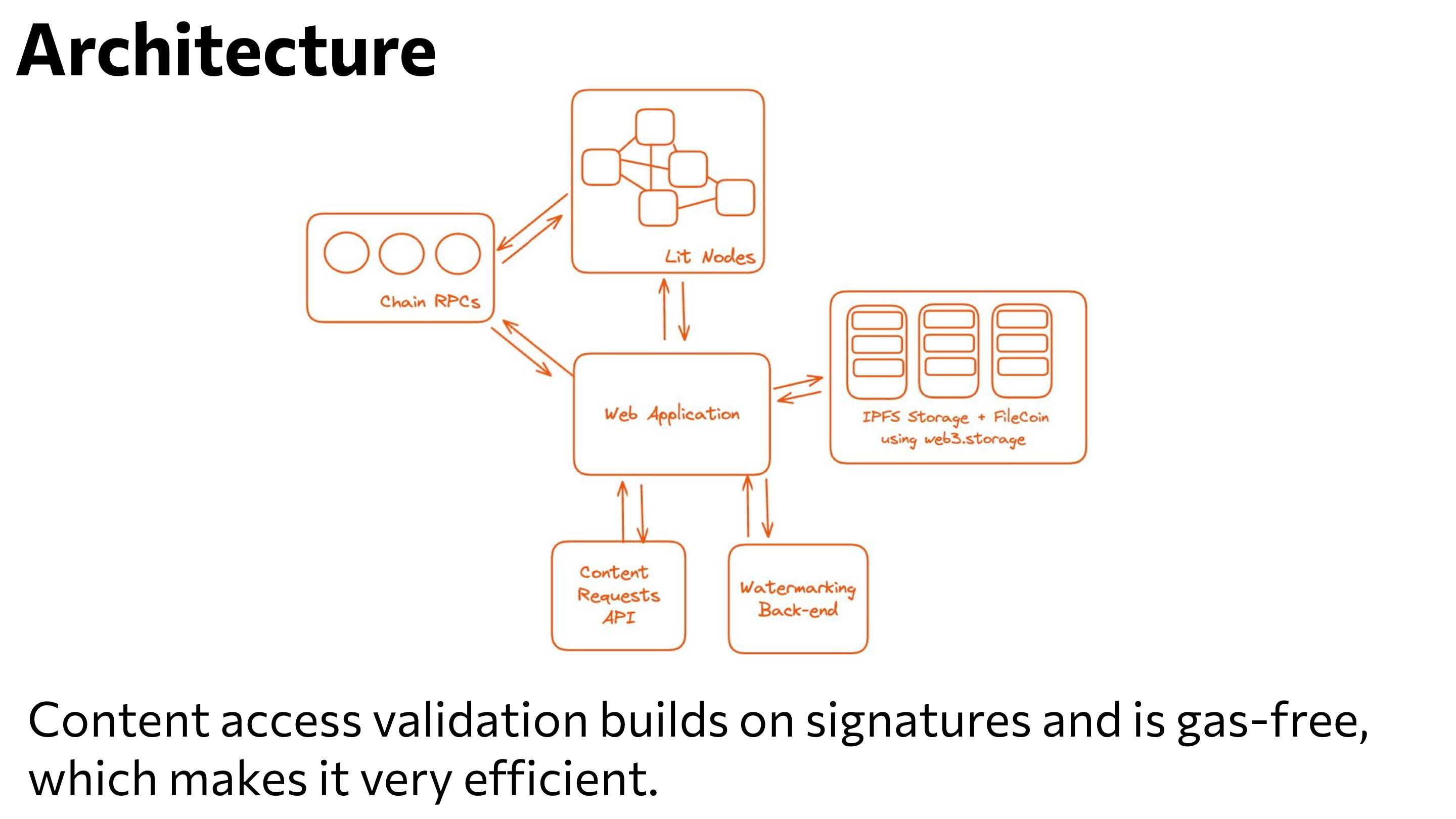
Architecture
Objective: Develop a system to enable intermediary-free distribution of private content copies between the distributor and clients, focusing on client identification and data privacy. This will ensure that each client can be accurately identified during specific copy leakage.
Github
Github monorepo https://github.com/lourenc/whataproof, which contains dApp front-end, backend APIs, Lit Protocol actions, and the infrastructure resources
How it's Made
Distribution Process:
- The distributor encrypts the original copy using the Lit Protocol and loads it to IPFS via web3.storage.
- A content web link is generated, which references the encrypted original copy, and the distributor shares it with consumers.
Consumer Requests Content Access:
- The consumer follows the content link provided by the distributor.
- The consumer requests access to the content.
Distributor Grants Access:
- The distributor reviews the requests list and decides whether to allow or deny access to the content.
- The distributor selects the access conditions, which include: a. By default, only the consumer is allowed to decrypt the content. b. Prohibiting content decryption if the client's APE ERC20 token balance is less than N tokens. c. Prohibiting content decryption if the client does not own an APE NFT. d. Based on quicknode API, disallowing encryption depends on on-chain activity, such as the number of weekly transactions.
- The contributor decrypts the original content copy.
- The original content is watermarked with the client's identifier by the contributor via LSB (Least Significant Bit) steganography.
- The watermarked copy is also encrypted and uploaded to IPFS, and decryption Lit Actions are deployed based on the previously selected access conditions.
Consumer Retrieves Watermarked Content Copy:
- The consumer follows the content link provided by the distributor.
- The consumer can decrypt the content copy if all access conditions are met.
Identifying Content Leaker:
Anyone can upload the leaked content copy to retrieve the leaker's identifier in content leakage.