zkyc
Uses TLS Notary to enable users to prove they've previously done a KYC. Service providers can save costs and improve onboarding by using our blinded tokens
Project Description
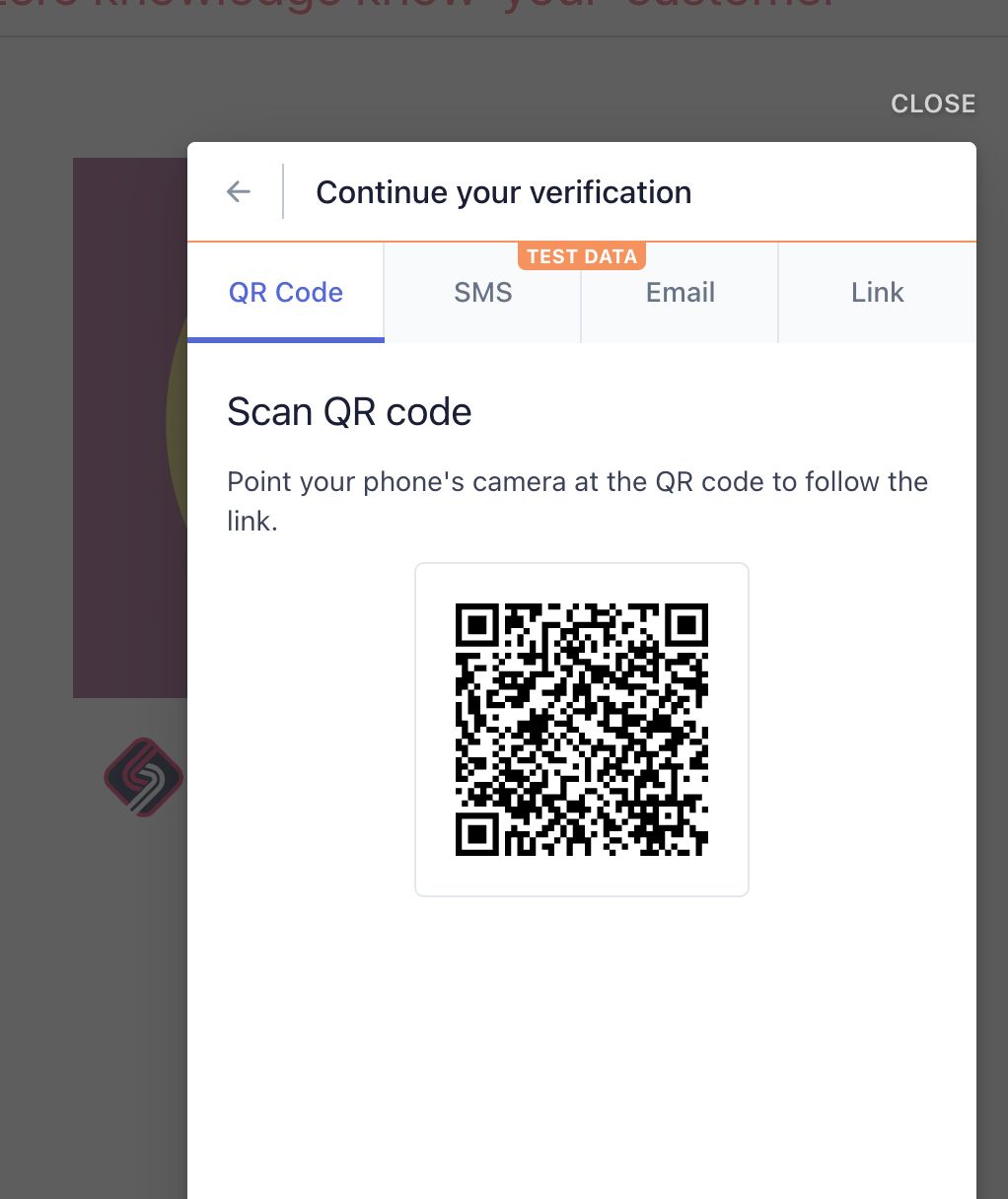
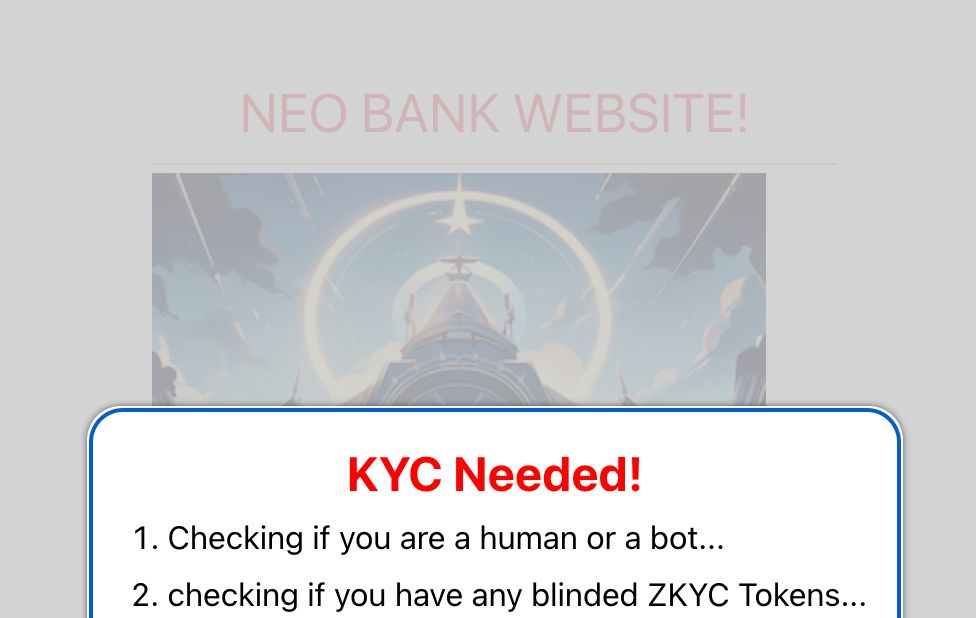
When building infrastrucrue at my last company, KYC & KYT regulations required us to use a company that charged us per-attestation. zkyc allows users to prove they have previously done a KYC "ceremony", and share those attestations securely and privately with any future service provider. No more selfies or passport photos!
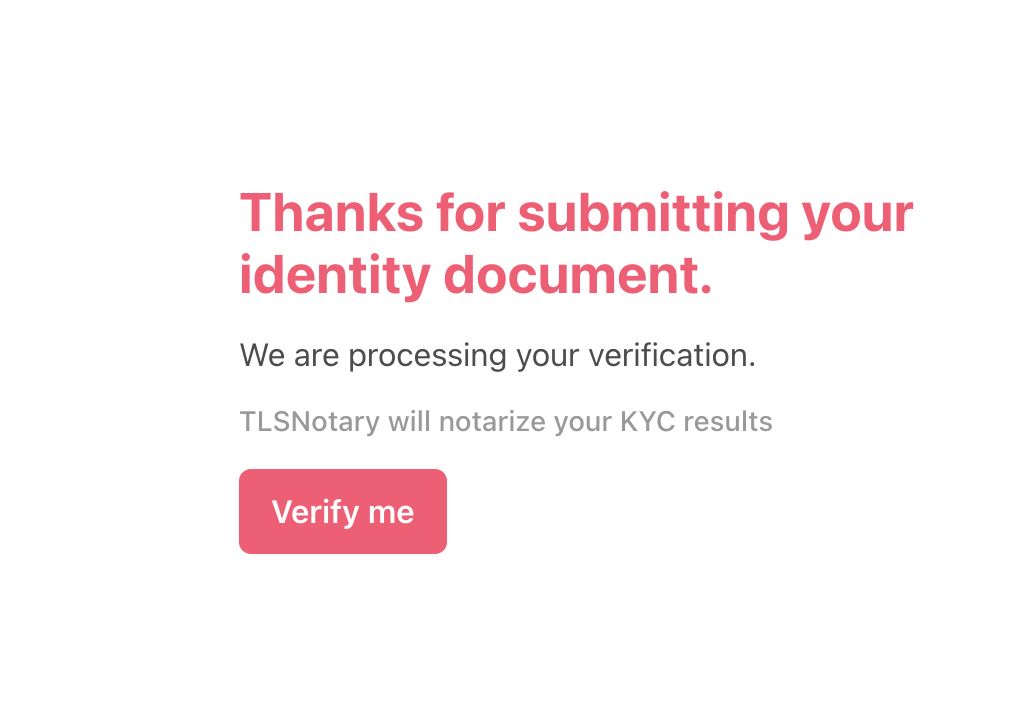
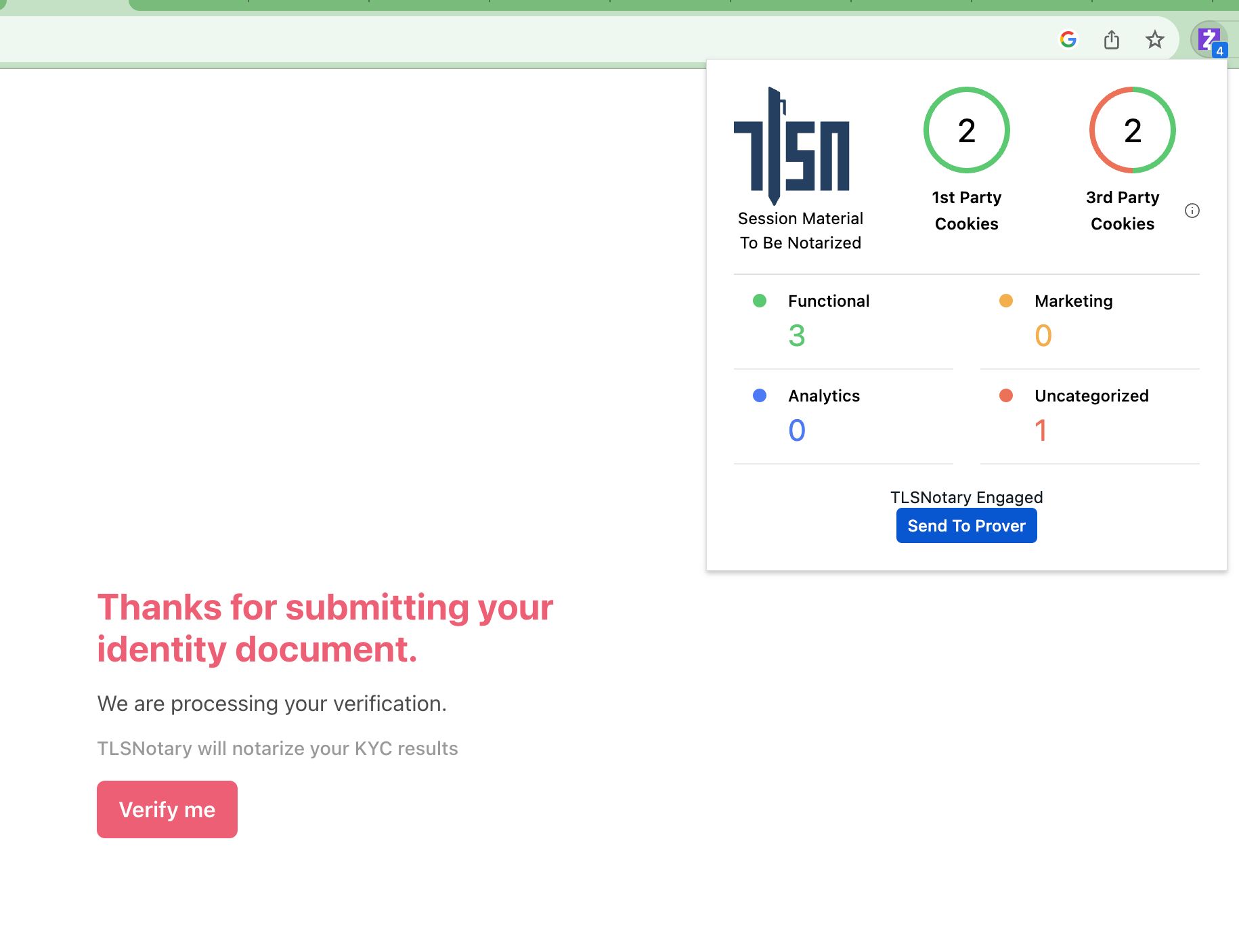
We used TLS Notary, which hijacks part of the TLS session key to create a MPC circuit that proves certain information was inside of that session.
We wanted a verifier to exist on chain but wasn't possible during the hackathon so we had to compromise and use the chromium implementation of privacy pass, a protocol that lets our off-chain verifier mint blinded tokens to users who attest successfully. Those tokens can be used seamlessly by any service provider who wants to speed up onboarding and reduce costs.
We burned about 12 hours trying to get the TLS Notary verifier compiled from rust to wasm using the arbitrum stylus / nitro / arbos machinery but due to size and wasm-bindgen and web-sys dependency issues we were unable to get it to work in time.
We think this is the first hackathon project to implement Private Stake Tokens and TLS Session MPC via TLS Notary.
How it's Made
4 webservers: https://kyc.codes https://notary.kyc.codes https://verifier.kyc.codes https://newbank.kyc.codes
2 Languages Rust, Typescript
ERC4626 vault (on stylus -- arbitrum goerli) for commitments and future payouts
A chrome browser extension that hijacks cookies out of KYC sessions and enables you to submit them to the verifier
Thanks to privy, our entire auth and wallet init stack was done with a few lines of code: users without wallets can use our tool without even knowing they are interacting with ethereum -- we have privy configured to pre-generate AA wallets for users so when they verify they already have on-chain real-estate.
HEAVY use of IPFS libp2p (helia) for in-browser WEBRTC transport and peer discovery -> we store the attestations on IPFS using a combo of IPLD and a DHT
Our last-mile hacky fix using tokes is using the freshly released chromium Trust Token implementation for blinded tokens (https://github.com/WICG/trust-token-api)
We tried to get the tlsnotary verifier compiled into wasm and onto the arbitrum rust L2 stylus, but due to time (and WASM size!) constraints we decided to use blinded tokens to enable users to spend KYC tokens signed by the notary.