Trustless Trust Exchange
A World of “Trustless“ Trust Exchange -Leverage reliable, third-party evaluations for trust-building -Fair and unbiased decision-making for DAO and project collaborations -Prevent false self-reporting and promote transparency -Escape the "honest people suffer" scenario
Trustless Trust Exchange
Created At
Winner of

📜 Scroll — Just Deploy

🏊♂️ Polygon — Pool Prize
Project Description
Decentralized Trust for Anonymous Workspaces
Traditional corporate organizations were closed entities that operated through centralized decision-making based on stock ownership and compensation through wages. In contrast, DAOs (Decentralized Autonomous Organizations) operate as open and fair entities that allow anyone to contribute, through a distributed decision-making process based on tokens and a reward system.
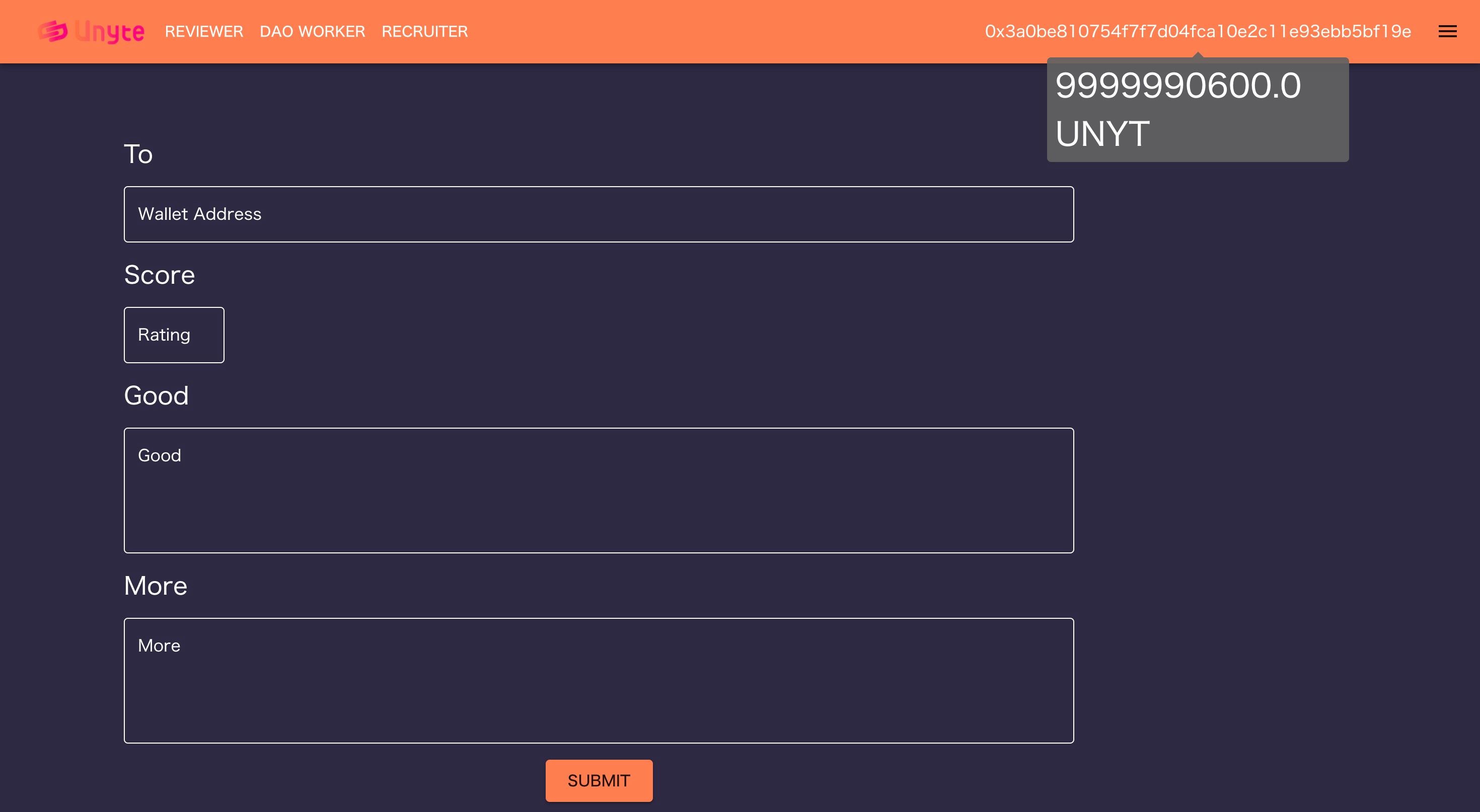
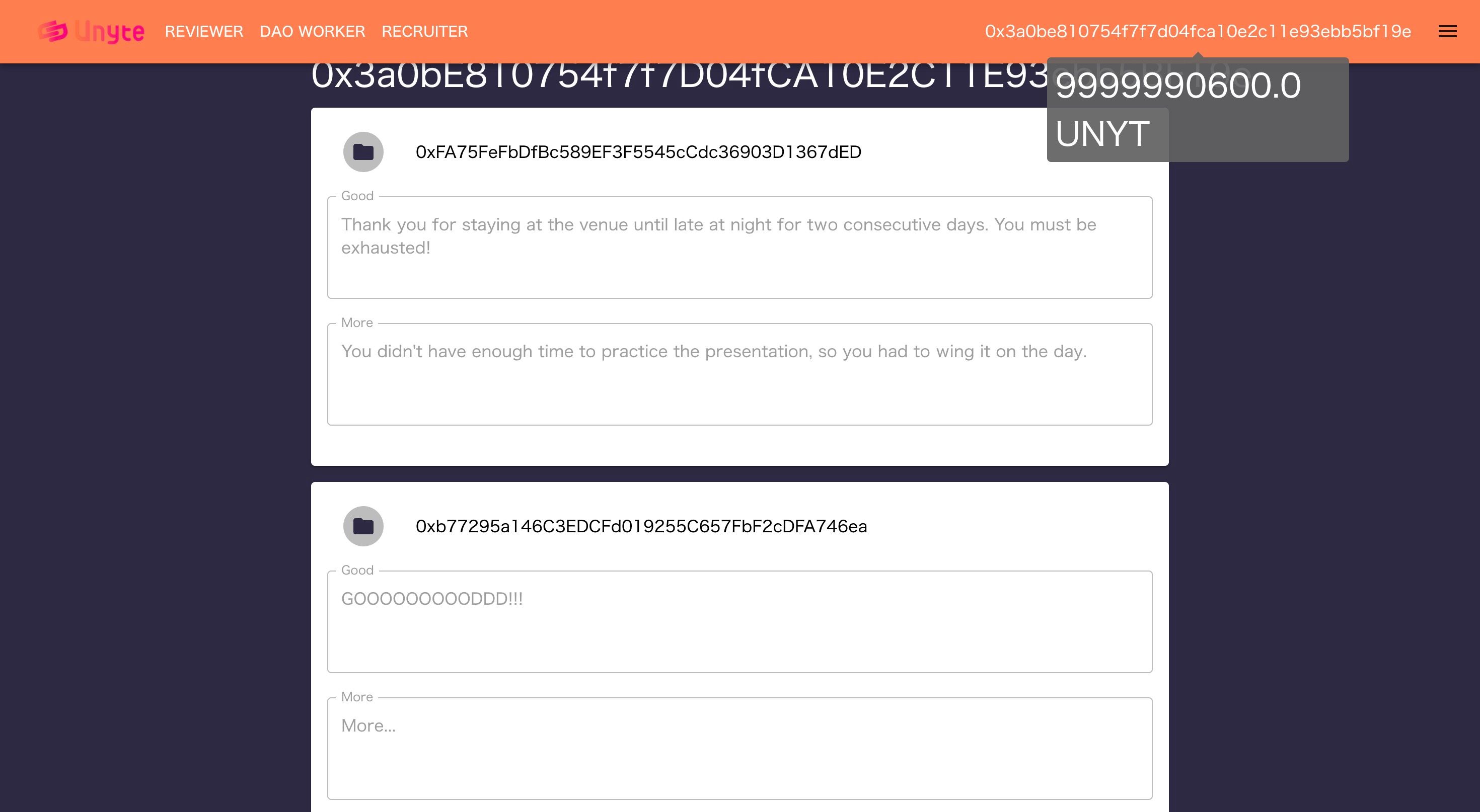
There has been a problem of sustainability in the operations of DAOs. To address this issue, we propose the implementation of a Decentralized Member Evaluation System.
Solution
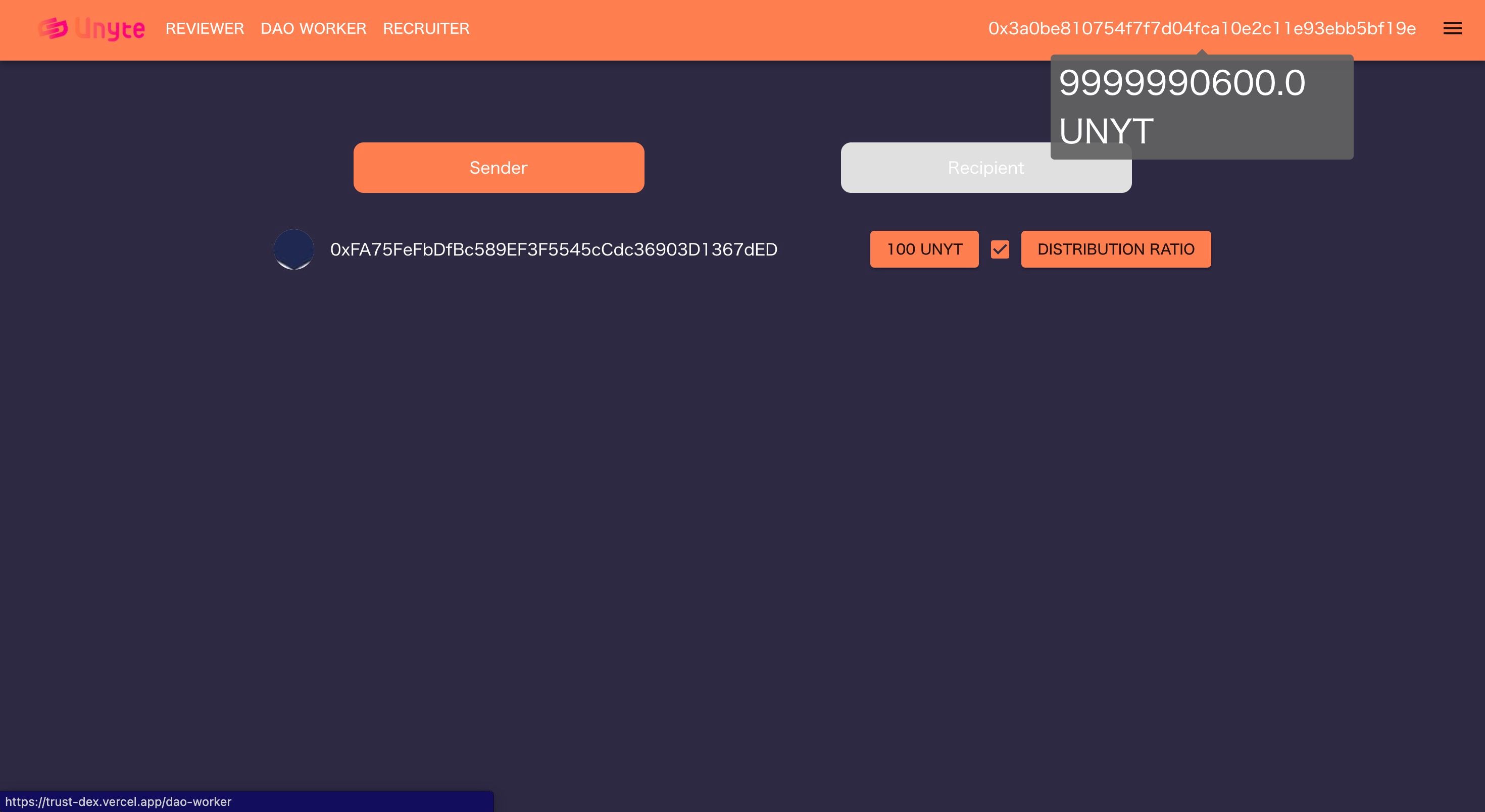
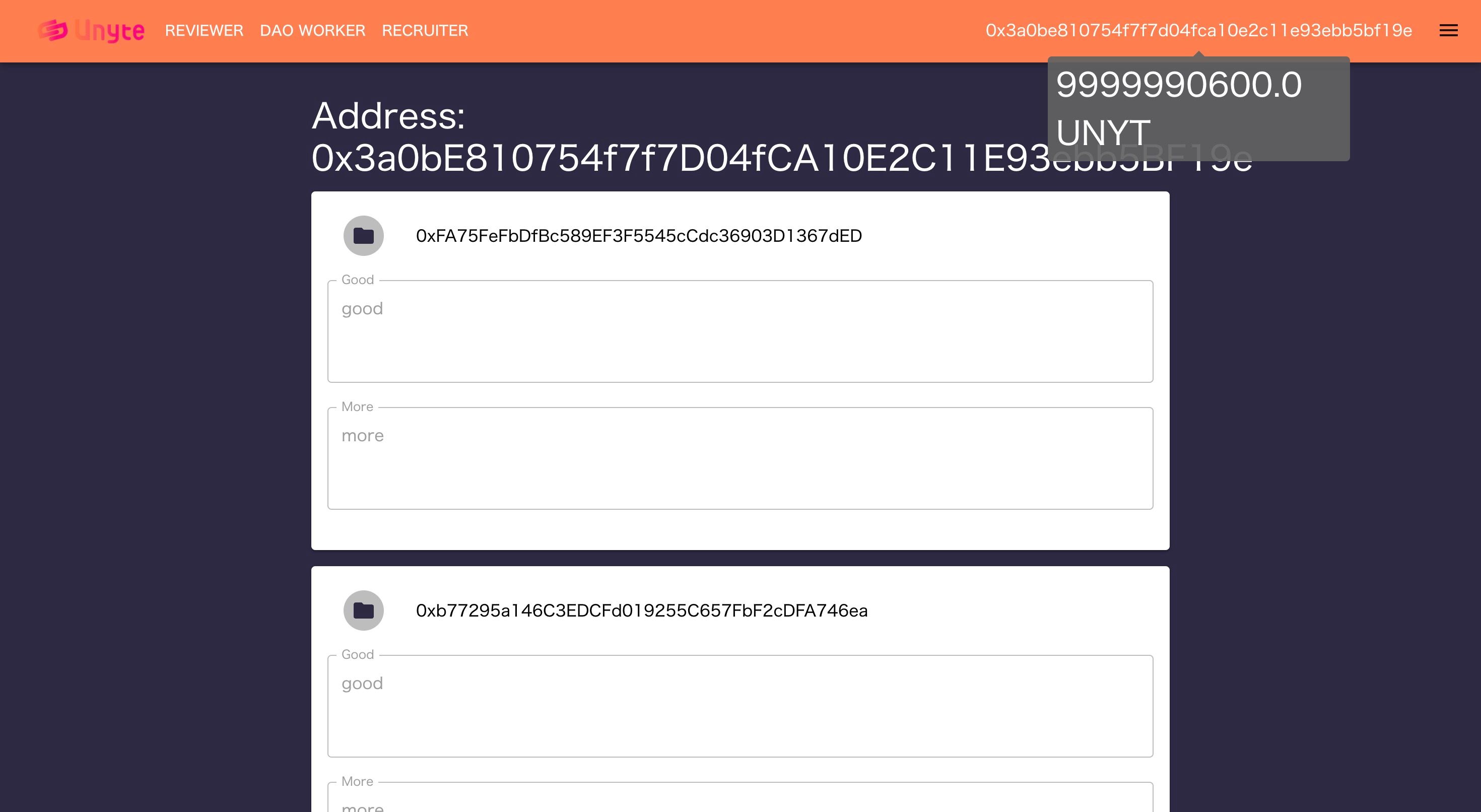
-Teammates can write encrypted evaluations for a user -Evaluations are stored securely and privately -Access evaluations using unique tokens sent to target user's wallet -Incentivize evaluation disclosure with token rewards
A World of “Trustless“ Trust Exchange
-Leverage reliable, third-party evaluations for trust-building -Fair and unbiased decision-making for DAO and project collaborations -Prevent false self-reporting and promote transparency -Escape the "honest people suffer" scenario
How it's Made
The data entered by the user is encrypted using Lit when it is stored on the chain. This is necessary to ensure that people who have not paid cannot see the data. Data is also stored in CELO. We had to pay a lot of gas money to fine-tune who to include in our own CVs, and we chose CELO for its performance, which is not available in other EVM chains. Normally, when the logic that only the token holder can decrypt data is expressed on the chain, it is difficult to securely store the data because the private key or the data that encrypts it is inevitably visible, but by using Lit, decrypting data only under certain conditions can be However, by using Lit, it is possible to decrypt data only under certain conditions, which is easier and more secure to implement.
Core Stack
-- React (version 18.2.0) -- Web3.js (version 1.9.0) -- Matarial UI (version 5.12.0) -- Emotion (version 11.10.6) -- lit-protocol -- ipfs
Supported Networks -- CELO and Scroll and any EVM