Trigon
Trigon is a Digital Identity Wallet on Polygon ID, managing verifiable credentials securely. It's a trusted platform for verifiers to validate zero-knowledge proofs, all within the Trigon ecosystem.
Project Description
Trigon is far more than a conventional digital self-sovereign identity wallet; it stands as a cutting-edge solution that seamlessly integrates with Polygon ID. Our core mission is unwavering: to address the ever-mounting concerns associated with identity theft and security vulnerabilities. We accomplish this mission by harnessing the formidable capabilities of blockchain technology and implementing state-of-the-art zero-knowledge proof protocols.
Trigon empowers individuals to effortlessly store, manage, and verify their verifiable credentials, all directly from the convenience of their mobile devices. This forward-thinking solution streamlines the complex process of handling personal data, ensuring users retain control of their own identities.
What truly sets Trigon apart is our innovative approach to identity verification. We've introduced a novel and pioneering method that sets new standards for security and trust in the digital transactions landscape. Additionally, we take immense pride in unveiling a groundbreaking feature: the issuance of photo-based verifiable credentials. This not only significantly enhances security but also ushers in a new level of convenience and accessibility within the existing Polygon ID system.
Our innovative verification method bridges the gap between traditional real-world identity verification and the web3 world. In the present Polygon ID system, verification is initiated by users scanning a QR code generated by the verifier. However, this approach isn't always practical, especially in real-life scenarios where verifiers must verify numerous holders using diverse matrices. To overcome this challenge, we've flipped the process on its head: now, users create a zero-knowledge proof QR code for verifiers to scan and authenticate the holder.
Our system further features a versatile verifier interface, where verifiers can create and manage their verification queries and accounts, all of which can be overseen by the issuer, a centralized authority, or a decentralized autonomous organization (DAO). This represents a proof of concept aimed at establishing seamless connectivity among the three key entities in the "triangle of trust": the issuer, verifier, and holder. Verifier queries are accessible to the holder, allowing them to create a zero-knowledge proof, which, in turn, can be scanned and verified by the verifier.
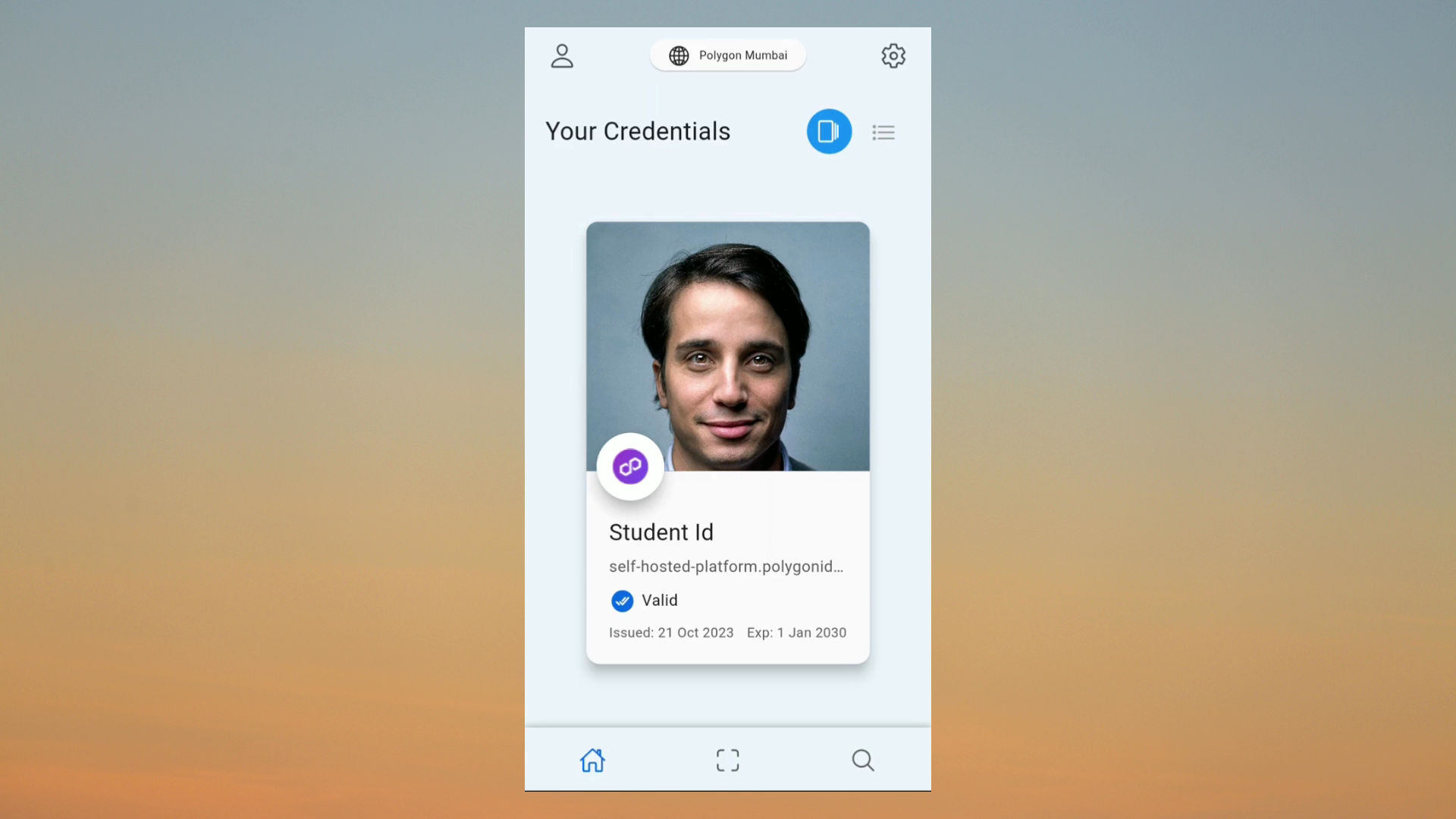
Another compelling feature of Trigon is the integration of Photo IDs within the verifiable credentials. This innovative addition addresses a critical security concern present in the current Polygon ID system. We adopt a model akin to government and other centralized authorities, where a photo ID is included as part of the verifiable credentials.
This enhancement ensures a higher level of confidence in verifying the identity of the holder. It significantly mitigates the risk of impersonation or fraudulent activity, as the photo ID serves as a visual confirmation that the person using the application is indeed the rightful holder of the credentials.
With this feature, Trigon not only offers advanced security but also aligns itself with well-established and trusted identity verification practices. It bridges the gap between traditional identification methods and the decentralized world, creating a more robust and dependable self-sovereign identity solution.
Our project, developed for an EthGlobal hackathon, marks a substantial leap forward in the realm of self-sovereign identity. With Trigon, we are primed to redefine how individuals manage and safeguard their personal information, ultimately empowering them in the digital age. We invite you to join us on this thrilling journey toward a more secure and confident digital future.
How it's Made
Project Development Details:
Technologies Used:
- Flutter: Flutter served as the frontend for the user interface.
- Polygon SDK: We harnessed Polygon ID SDK, a collection of Flutter-based tools, including libraries, code samples, APIs, and documentation, to develop the Polygon ID Wallet App.
- Node.js: Node.js was employed to manage the backend, initialize the logic, create API endpoints, and store data in the database.
- MongoDB: MongoDB played a pivotal role in storing the verifier's directory and their queries.
How We Built It:
Our development process involved a meticulous approach, incorporating a range of cutting-edge technologies. Here's a breakdown of how we brought our project to life:
-
Leveraging Polygon ID Wallet SDK: We utilized the Polygon ID wallet SDK to build the application, enhancing it with our own solutions using Dart and Node.js.
-
Innovative Verification Method: We introduced an innovative verification method that bridges the gap between traditional real-world identity verification and the web3 world. In the conventional Polygon ID system, verification is initiated when users scan a QR code generated by the verifier. However, this approach is not always practical, especially when verifiers must authenticate numerous holders with diverse matrices. To address this challenge, we turned the process on its head. Now, users create a zero-knowledge proof QR code for verifiers to scan and authenticate the holder.
-
Versatile Verifier Interface: Our system includes a versatile verifier interface, allowing verifiers to create and manage verification queries and accounts. These functionalities can be overseen by the issuer, a centralized authority, or a decentralized autonomous organization (DAO). This concept aims to establish seamless connectivity among the three key entities in the "triangle of trust": the issuer, verifier, and holder. Verifier queries are accessible to the holder, enabling them to create zero-knowledge proofs, which can be scanned and verified by the verifier.
-
Photo-Based Verifiable Credential: A noteworthy feature of Trigon is the integration of photo IDs within verifiable credentials. This innovative addition addresses a critical security concern present in the current Polygon ID system. We adopted a model akin to government and other centralized authorities, incorporating a photo ID as part of the verifiable credentials. This enhancement enhances the confidence in verifying the holder's identity, significantly reducing the risk of impersonation or fraudulent activity. The photo ID serves as a visual confirmation that the person using the application is indeed the rightful holder of the credentials. This feature not only offers advanced security but also aligns with well-established and trusted identity verification practices, bridging the gap between traditional identification methods and the decentralized world. This creates a more robust and dependable self-sovereign identity solution.