Bug Pointer
Bug Pointer: the Sybil attack resistant bug bounty platform. With proof of personhood, it ensures fair rewards, solving platform issues. Say goodbye to injustice, welcome fair hacker rewards.
Bug Pointer
Created At
Winner of

🥈 Worldcoin — Honorable Mentions

5️⃣ Chainlink — Best Hack
Project Description
Introducing our product that combines a bug bounty platform with a cutting-edge ZK proof of personhood system. With this innovative tool, we efficiently combat the challenge of Sybil attacks, ensuring another level of security and fairness.
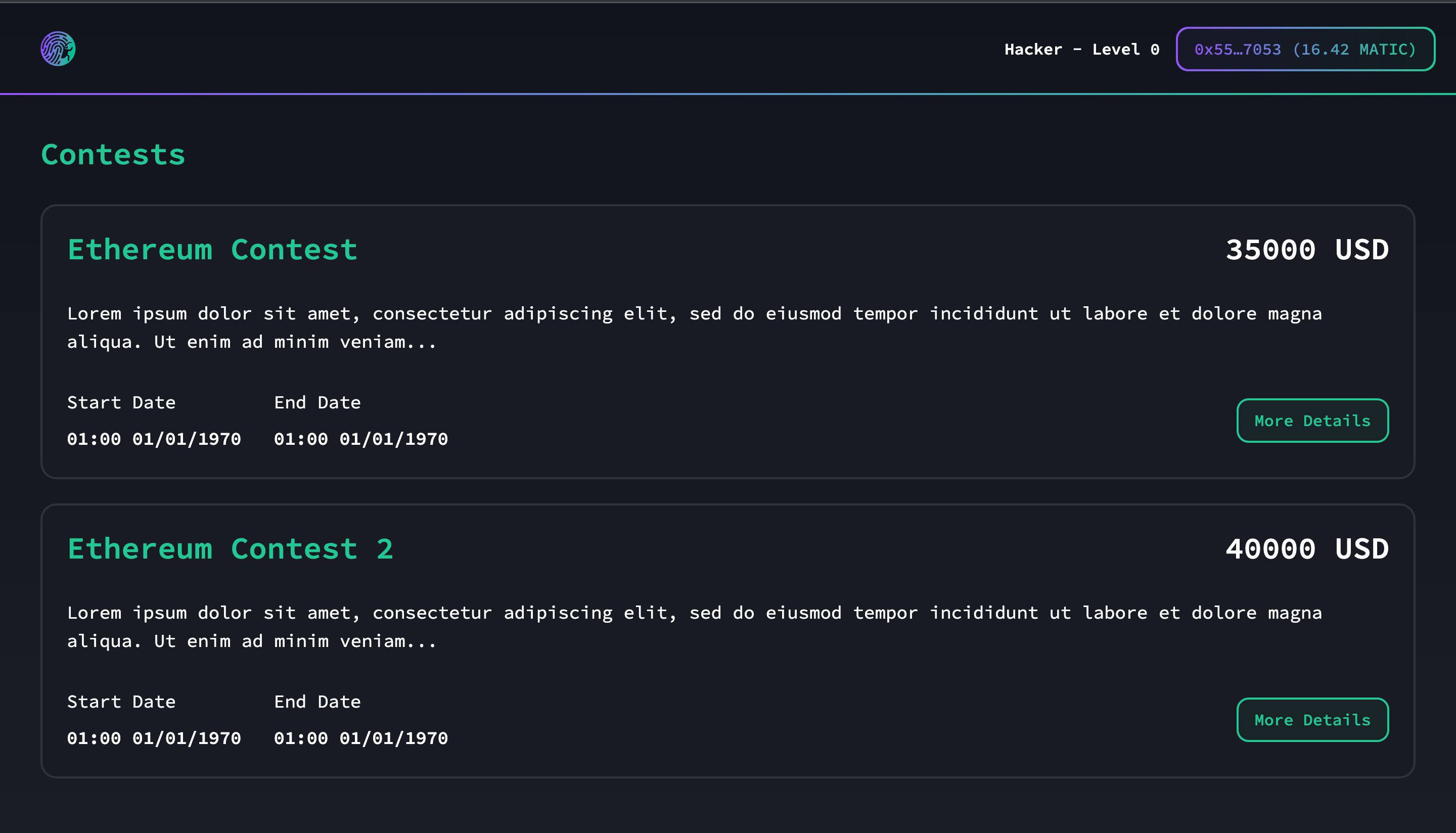
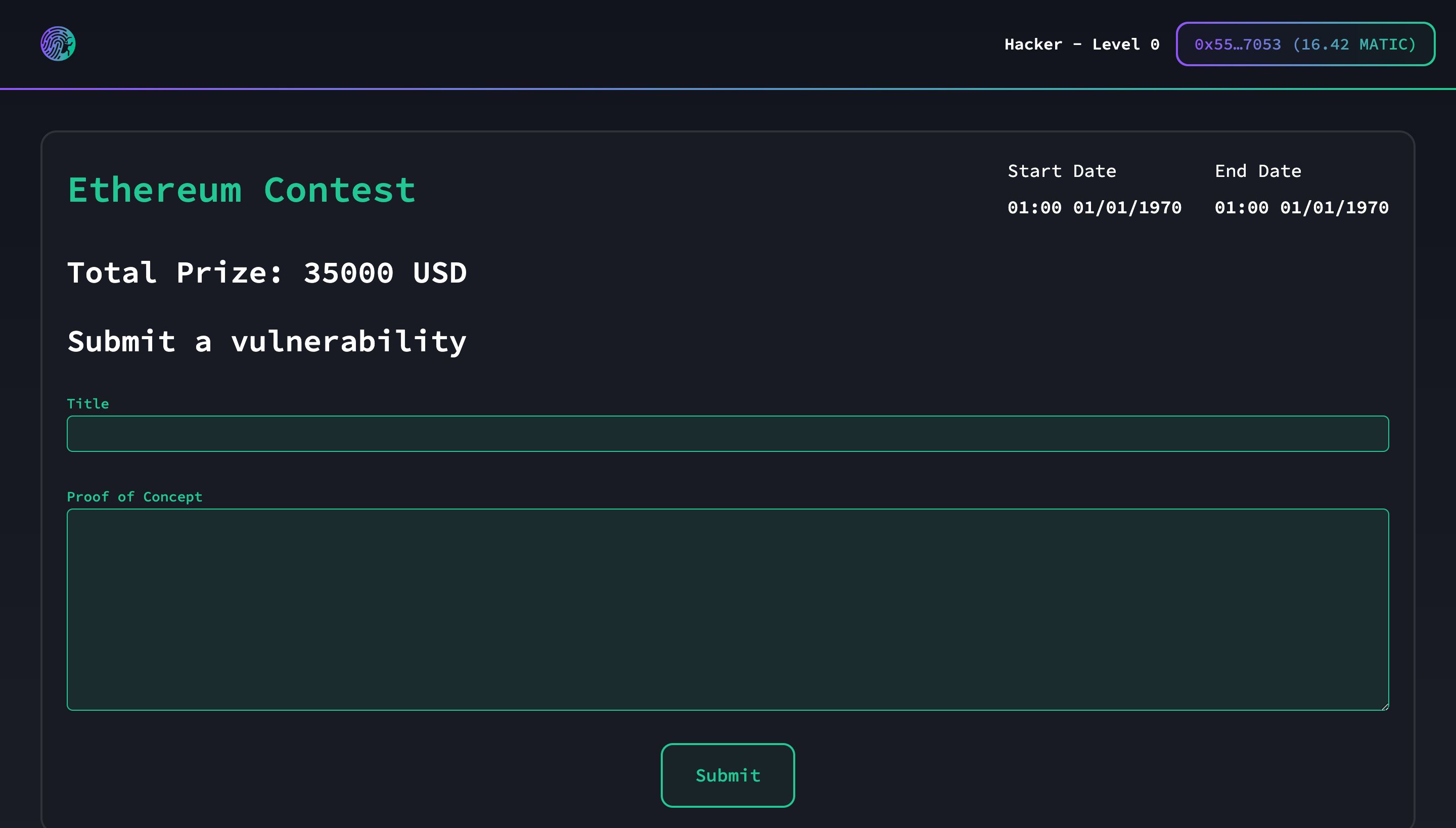
We can create contests with bounties for developers and judges, who are the two players in our game. Before the start of the contests, we randomly selected the judges who would evaluate the contests. We utilized the VRF (Verifiable Random Function) Chainlink Technology to ensure the random selection of judges. This process is required to deploy the contest. After the contest starts, developers can analyze the smart contracts within the scope and submit their vulnerabilities. They have a specified time period, defined at the beginning of the contest, to submit all the vulnerabilities they have found. Once this period is over, judges can begin their work. When the judges have completed their analysis, the results are published on the leaderboard, and all developers can view them on their dashboards. Before we created our product, developers could submit their vulnerabilities using different wallets and potentially receive multiple rewards. This posed a problem because all contests were supposed to be fair. How can we resolve this problem? By integrating the Worldcoin project with our advanced World ID verification system, we take the concept of proof of personhood to the next level. Our seamless integration allows users to validate their identity securely and reliably, enhancing trust and mitigating fraudulent activities. With this technology, we can obtain proof that a human is a real unique individual.
In summary, with our platform, the elimination of the persistent problem encountered in many bug bounty platforms becomes a reality. By establishing a ZK proof of personhood mechanism, we eliminated Sybil attacks, wherein malicious actors create multiple fake identities to manipulate the reward system. This not only safeguards the integrity of the bug bounty process but also ensures that the rewards are distributed fairly among the deserving participants.
How it's Made
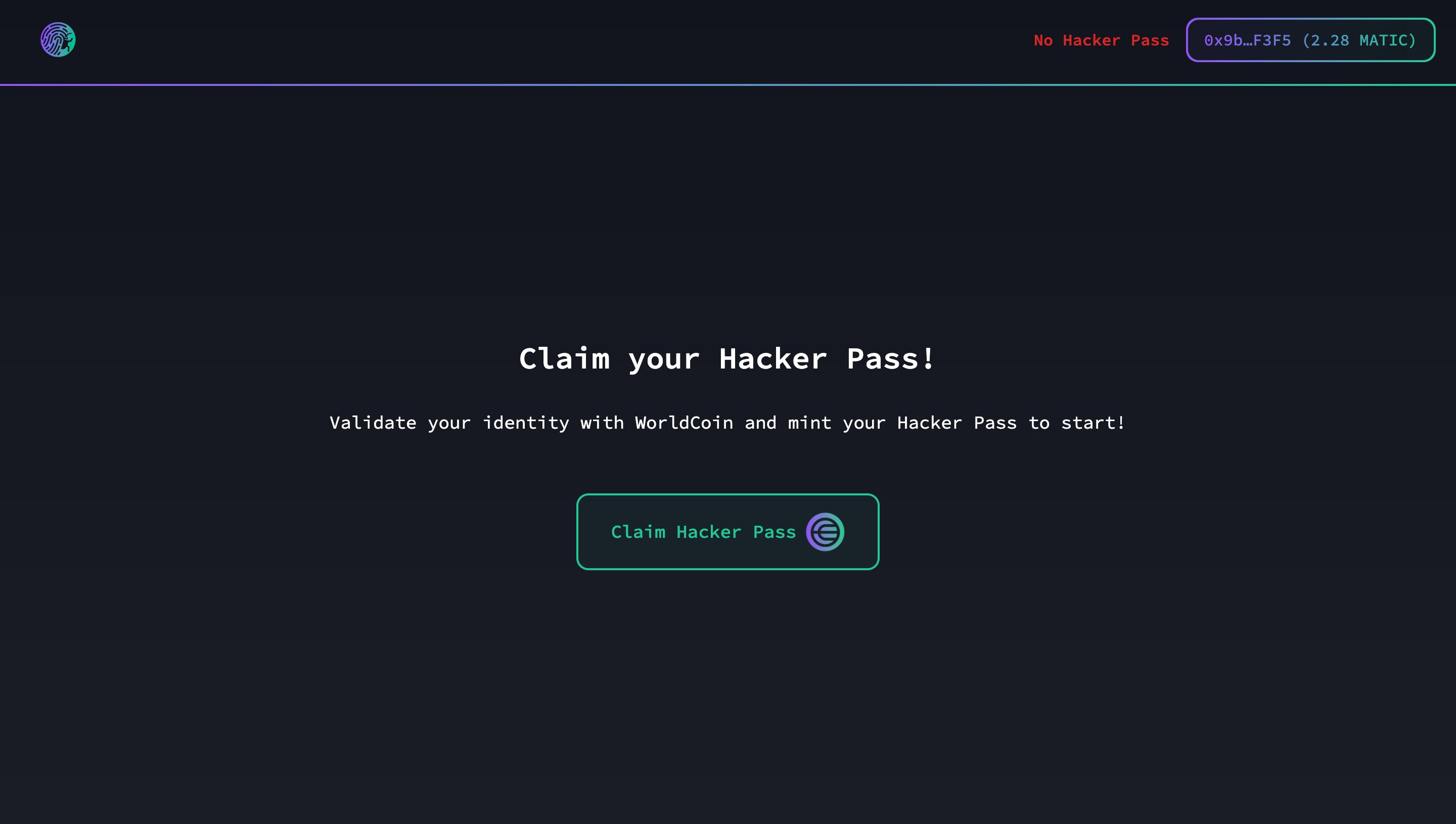
We created a bug bounty platform and incorporated KYC-free authentication. However, we ensured that developers submitting vulnerabilities could only do so from a single wallet. Leveraging zero knowledge proofs provided by WORLDCOIN technology, we can verify our unique human identity and thereby establish resilience against Sybil attacks. If a developer creates multiple wallets, as they are only a single human, they can only prove their identity in one of those wallets.
Before the start of the contest, it is a prerequisite to have the judges selected. To eliminate any form of manipulation or potential conflicts of interest in the judge selection process, we have decided to implement Chainlink's VRF (Verifiable Random Function) technology, which generates random numbers. The judges are organized in an array, and when the numbers are provided by Chainlink's VRF, they determine the selected positions within the array. The judge occupying the corresponding position is then chosen. This approach enables us to decentralize the decision-making power regarding the selection of contest judges.
The team considers the proposed solution particularly ingenious because bug bounty contests are increasingly utilized by developers, and as a consequence, the problem intensifies.